Building a SaaS product that serves multiple customers from one codebase sounds simple-until one tenant accidentally sees another’s data. Or worse, their billing spikes because the AI didn’t limit resource usage. This isn’t hypothetical. In 2024, 34% of SaaS security incidents came from broken multi-tenancy, according to AWS. And with AI-assisted "vibe coding" now speeding up development, the risk is higher than ever.
What Multi-Tenancy Really Means (And Why It’s Not Optional)
Multi-tenancy isn’t a feature. It’s the foundation. It means one instance of your software serves dozens, hundreds, or thousands of customers-each with their own data, settings, branding, and users-without mixing anything up. If you’re building a SaaS app today, you’re almost certainly building a multi-tenant system. Gartner says 73% of new SaaS apps use this model, up from 61% just a year ago.
But here’s the catch: if you don’t design it from day one, you’ll pay for it later. Aatir, a developer who tried adding multi-tenancy to an existing app, called it "a hot mess" that forced him to start over. That’s not an outlier. On Reddit, u/cloud_architect99 built a dashboard in two days using AI tools-then spent a full week fixing data leaks. The problem? He assumed the AI would handle isolation. It didn’t.
The Three Ways to Isolate Tenants (And Which One to Pick)
There are three main ways to keep tenant data separate. Each has trade-offs in cost, complexity, and scalability.
- Database-per-tenant: Each customer gets their own database. This is the safest. Easy to back up, audit, and migrate. But it’s expensive. You’re running dozens of database instances. Not practical for small SaaS startups.
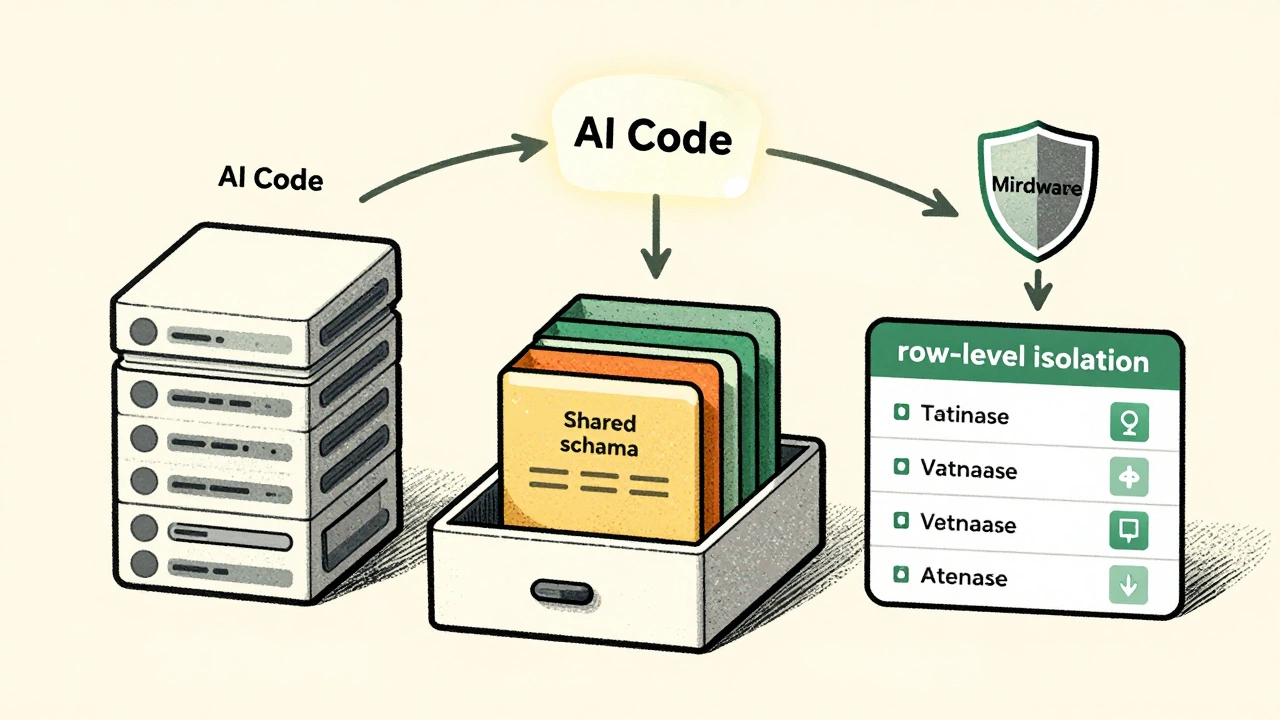
- Shared database, separate schemas: One database, but each tenant gets their own schema (like a folder inside the database). Good balance. Easier to manage than separate databases. PostgreSQL supports this well. Used by many mid-sized SaaS apps.
- Shared database, row-level isolation: All tenants share the same tables. Every record has a
tenant_id. Queries must always filter by it. This is the most cost-efficient-and the most error-prone. One missing WHERE clause, and boom: data leak.
Most vibe-coded SaaS apps go with row-level isolation. It’s cheap, fast, and AI tools can generate the code quickly. But here’s the trap: if you don’t enforce it at the database level, the AI might forget. GitHub’s research shows AI assistants correctly implement row-level security only 87% of the time-when prompts are clear. Without strict instructions, that number drops fast.
Authentication: One System, Many Tenants, Many Identities
Each tenant needs their own login system. Maybe they use Google. Or Microsoft. Or their own SSO. Your app can’t force everyone into one box.
Traditional approaches use custom auth servers. Vibe coding leans on tools like Supabase Auth or Firebase Auth. These handle email verification, password resets, and OAuth out of the box. But they’re not magic. You still need to tie every user to their tenant.
Here’s what works: Use an API gateway to intercept every request. Extract the tenant ID from the subdomain (like client1.yourapp.com) or from a JWT token. Then inject that ID into every database query. Don’t trust the frontend. Don’t trust the AI. Build middleware that enforces it.
One developer on Hacker News lost $12,000 in AWS bills because his AI-generated auth system didn’t link users to tenants. One user signed up, got access to everything. That’s not a bug. That’s a lawsuit waiting to happen.
Cost Controls: Why Your AI Might Bankrupt You
AI tools are great at writing code. They’re terrible at understanding economics.
Imagine you build a SaaS analytics tool. One tenant uploads 50GB of data. Your AI-generated backend spins up 10 serverless functions to process it. No limits. No throttling. No alerts. That tenant runs up a $5,000 bill in one night. You don’t charge them for it. You eat it.
That’s not speculation. It happened. u/foundersadness reported exactly this on Reddit in July 2024. The fix? Meter usage. Track how much storage, compute, and API calls each tenant uses. Set hard caps. Kill processes that go over. Use serverless functions (like AWS Lambda) to handle this automatically.
Bitcot’s system, for example, uses automated tenant provisioning that includes: setting resource quotas, enabling usage alerts, and configuring billing triggers-all in under 90 seconds. You can’t do that by guessing. You need to define it in your AI prompts: "Limit each tenant to 100 serverless invocations per day. Send alert at 80%."
Vibe Coding: Speed vs. Safety
Vibe coding lets you generate a working multi-tenant app in hours, not weeks. Nhad Iqbal built a full HRMS system in under 24 hours using AI. That’s incredible. But speed isn’t free.
Frontegg’s CTO, Eran Stiller, warns that vibe coding creates "black box architectures." Developers don’t understand what the AI wrote. They can’t audit it. They can’t fix it when it breaks.
Here’s the reality: AI is a co-pilot, not a captain. You still need to know how multi-tenancy works. You still need to know what a row-level security policy looks like. You still need to know why tenant_id must be in every query-and why tenant_name is a security disaster.
GitHub’s AI research team found that when developers gave precise prompts-like "implement PostgreSQL row-level security with tenant_id as discriminator and never allow cross-tenant queries"-AI got it right 87% of the time. Without that specificity? It dropped to 41%.

How to Do It Right: A Step-by-Step Guide
Don’t wing it. Even with AI. Here’s how to build a secure, scalable, cost-controlled multi-tenant SaaS using vibe coding:
- Define your isolation strategy first. Pick row-level, schema, or database-per-tenant. Write it down. Don’t let the AI decide.
- Write explicit AI prompts. Don’t say "build multi-tenancy." Say: "Generate PostgreSQL row-level security policies using tenant_id as the discriminator. Every SELECT, UPDATE, DELETE must include WHERE tenant_id = current_tenant()."
- Build tenant-aware middleware. Create a function that pulls tenant context from headers or subdomains and injects it into every request. Test it with fake data.
- Set up automated tests. Write a test that simulates Tenant A querying Tenant B’s data. It must fail. If it doesn’t, your isolation is broken.
- Implement usage limits. Use serverless functions to track storage, compute, and API calls per tenant. Set caps. Send alerts.
- Run manual penetration tests. Hire a freelancer for $500 on Upwork to try breaking your app. Most AI-generated apps fail this test.
Bitcot’s team spent 15-20 hours designing the architecture before writing a single line of AI-generated code. That investment saved them 200+ hours of rework.
The Bottom Line: AI Doesn’t Replace Architects
Vibe coding is powerful. It’s fast. It’s changing how SaaS is built. But it doesn’t replace understanding. If you don’t know how tenant isolation works, you shouldn’t be using AI to build it.
Companies that succeed with vibe coding don’t rely on the AI to get it right. They use AI to execute their plan-fast. They know the rules. They write precise prompts. They test everything.
And they never, ever assume the code is safe just because it runs.
Can I add multi-tenancy to an existing single-tenant app?
Technically, yes. Practically, no. Most attempts end in disaster. You’ll need to rewrite every database query, add tenant context to every API call, migrate data, and test for leaks. Aatir’s experience is common: it’s faster and cheaper to start over. If you’re building for multiple tenants, design it that way from day one.
What’s the biggest mistake people make with vibe-coded multi-tenancy?
Assuming the AI will handle isolation automatically. AI tools are great at generating code, but they don’t understand security context. If you don’t specify "tenant_id must be in every WHERE clause," the AI might leave it out. That’s how data leaks happen.
Is row-level security enough for GDPR compliance?
It’s necessary, but not sufficient. GDPR requires data to be stored and processed within specific regions, with clear consent tracking. Row-level security keeps data isolated, but you still need to log data access, allow deletion requests, and ensure backups are encrypted and tenant-scoped. Use tools like Supabase or Firebase that offer built-in compliance features.
How do I test if my tenant isolation is working?
Write automated tests that simulate cross-tenant access. For example: log in as Tenant A, then send a request with Tenant B’s ID in the URL or headers. If the system returns Tenant B’s data, your isolation is broken. Also, use database query logs to check for missing tenant_id filters. Tools like pgBadger can help spot these in PostgreSQL.
Why do some developers say vibe coding is risky for SaaS?
Because it hides complexity. A developer might generate a working app in a day, but not understand how the authentication flow works or why the database queries are secure. When something breaks-like a tenant sees another’s data-they can’t fix it. That’s why 63% of enterprise architects distrust AI-generated isolation mechanisms. Speed without understanding is dangerous.



Ashley Kuehnel
9 December, 2025 - 10:19 AM
Yikes, I just realized my last project had a tenant_id bug because I trusted the AI too much. I thought it would just "get it" but nope, one missing WHERE clause and boom-customer data leaked. Learned my lesson the hard way. Always double-check the SQL. Always.
adam smith
9 December, 2025 - 15:33 PM
Multi-tenancy is important. You must have isolation. Failure leads to legal issues. Use databases properly.
michael Melanson
11 December, 2025 - 11:43 AM
I’ve seen this exact scenario play out twice. The first time, a startup used row-level isolation without middleware enforcement. They got breached via a misconfigured API endpoint. The second time, someone used AI to generate auth logic and forgot to bind user-to-tenant context. Both cost six figures in downtime and legal fees. The fix isn’t complex-it’s discipline.
lucia burton
11 December, 2025 - 18:20 PM
Let’s be real-vibe coding is the new black box development. We’re outsourcing architectural thinking to LLMs and then acting surprised when the system collapses under compliance pressure. Row-level security isn’t a toggle you flip in a prompt. It’s a cultural commitment. You need audit trails, query sanitization, automated test suites that simulate cross-tenant attacks, and engineers who understand the difference between a tenant_id and a tenant_name. If your AI-generated code doesn’t have a tenant_id in every single SELECT, UPDATE, and DELETE, you’re not building SaaS-you’re building a liability.
Denise Young
12 December, 2025 - 10:02 AM
Oh wow, so the AI didn’t read the fine print again? Shocking. I mean, did you really think a language model that can’t tell the difference between a coffee mug and a hat is going to understand GDPR? "Hey AI, make sure no one sees another tenant’s data." And it’s like, "Sure thing, human. I’ll just assume you meant to add tenant_id to every query... oh wait, I forgot. My bad. Here’s your $12k AWS bill."
Look, if you’re going to use AI to build infrastructure, you need to be the architect, not the cheerleader. Write prompts like you’re writing a court order. "Every query must include tenant_id AND fail if tenant_id is null." No room for interpretation. And then test it. Like, actually test it. Not just "it runs"-test if Tenant A can access Tenant B’s data. If they can, you’re not a developer-you’re a liability waiting to be sued.
Sam Rittenhouse
12 December, 2025 - 14:48 PM
I used to think vibe coding was magic. Then I watched a colleague build a full HR platform in 18 hours using AI. It worked. Until a user from Company X accidentally saw payroll data from Company Y. The entire team panicked. We spent three weeks rewriting every query, adding middleware, and writing tests. The worst part? The AI didn’t make a mistake-it made a hundred tiny ones, all invisible until something broke. Now I treat AI like a junior dev who needs constant supervision. I write prompts with surgical precision. I review every line. I test for edge cases. Speed is great-but not if you’re building on sand.
Peter Reynolds
13 December, 2025 - 17:42 PM
row level security is fine but you need to make sure the middleware is solid. also test with fake data. i did this once and it worked until someone used a header trick. now i use subdomain + jwt + middleware. no exceptions. also use serverless for cost control. it auto scales and kills overuse. simple.
Fred Edwords
13 December, 2025 - 23:29 PM
It is imperative to underscore that the implementation of row-level security, when leveraging AI-assisted development paradigms, must be accompanied by rigorous, automated, and deterministic validation protocols. The 87% success rate cited in GitHub’s research is statistically misleading unless contextualized by the precision of the prompt engineering employed. Moreover, the absence of tenant_id in even a single database query constitutes a critical vulnerability, not a minor oversight. It is therefore not merely advisable but mandatory to enforce query sanitization via middleware, to mandate tenant context injection at the API gateway layer, and to conduct penetration testing using adversarial input vectors. Failure to do so is not negligence-it is recklessness.
Sarah McWhirter
15 December, 2025 - 18:14 PM
Wait… so you’re telling me AI is writing code that controls how people’s private data is stored… and nobody’s checking if it’s actually secure? That’s not a bug. That’s a government surveillance tool waiting to be weaponized. Did you know that the same AI that generated your multi-tenant app also trained on leaked corporate databases? It’s not just forgetting tenant_id-it’s learning how to exploit it. I’ve seen the dark web forums. Hackers are already reverse-engineering vibe-coded SaaS apps. They don’t need to brute force-they just wait for the AI to slip. And you’re just… trusting it? You’re not building software. You’re building a digital trap for your customers. Wake up.